Introduction
Hello guy’s We are excited to announce the collaboration between computertipstricks.tech on this blog post! We have bring unique perspectives and expertise to the table, making for a dynamic and informative content.
computertipstricks.tech is known for their Computer Skills, Programming Languages, Computer Tips and Tricks, etc. Together, they will dive into topic of How to Use : Nmap for ports and Network scanning , exploring the latest trends and ideas in the field. So sit back, grab a cup of coffee, and get ready to dive into the world of Nmap.

Network and Port scanning is like going around a house and observing which doors 🚪 and windows are open and who is standing on them.
Here, doors and windows are similar to ports and the person standing on the door can be understood as the services running on the specific ports.
There are various tools and methods to scan a host/server/web-server. Let’s begin going through them one by one.
In the Network ans Port scanner section of Information gathering tab of our Kali Linux, there are mainly two tools in the list.
N-map is one of those tools that a pen-tester can’t live without. It has so many modules and modes, that it does everything. It can scan open ports, identify what services is running on the ports, it even has various scripts that can make your life ultra easy while scanning. No matter, how much I exaggerate, n-map always exceeds your expectations. It’s so good that it is even shown in movies with hacking scenes. If you visit N-map Official Website, you can know more about it’s development and uses in a orderly manner.
It can be used for the following purposes:
- Real time information of a network
- Detailed information of all the IPs activated on your network
- Number of ports open in a network
- Provide the list of live hosts
- Port, OS and Host scanning
Also Read : 50+ Awesome Tor Tools For Browsing Dark-web Safely.
In addition to the interesting ports table, N-map can provide further
information on targets, including reverse DNS names, operating system
guesses, device types, and MAC addresses.
A typical N–map scan is shown in Example 1. The only N-map arguments used
in this example are -A, to enable OS and version detection, script
scanning, and trace-route; -T4 for faster execution; and then the
hostname.
Moving forward, we should learn some basic commands.
1. N-map basic scan
You can use either hostname(DNS) or host-IP(preferably ipv4).
nmap <hostname/host_IP>

N-map basic scan with -v (verbosity)
nmap <hostname/host_IP> -v

You can see the difference between both the output. So, always use -v tag. You can also increase the verbosity level by adding more v like this.
nmap <hostname/host_IP> -vvv
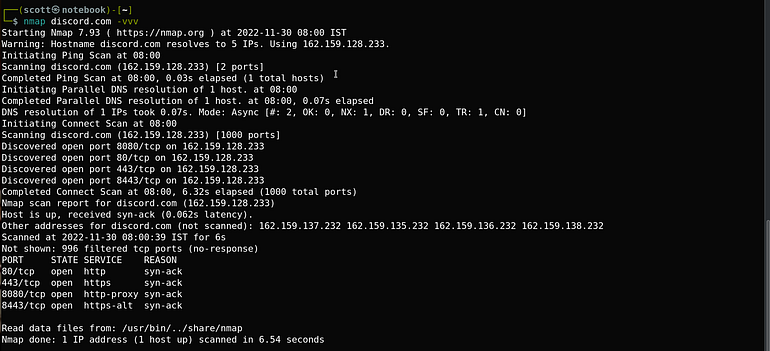
2. N-map to scan multiple hosts
All you have to do is type the next IPs in your syntax like this.
nmap <hostname1/host_IP1> <hostname2/host_IP2> <hostname3/host_IP3>

3. N-map to scan the whole subnet.
At the end of the syntax add ‘*’.
nmap 192.53.165.*
I did a random subnet scan and just look at the output, I got!
Tip- Don’t forget to add verbosity (-v) tag in your syntax.
4. Using Nmap to scan firewall settings of a host.
Use ‘-sA’ tag in the syntax, and you will need the root* privileges to do this type of scan.
sudo nmap -sA 103.76.228.244

5. To scan from a file
Use ‘-iL’ in your syntax.
nmap -iL <filename.txt>

6. Nmap Aggressive Scan
Here -A indicates aggressive, it will give us extra information, like OS detection (-O), version detection, script scanning (-sC), and traceroute (–traceroute). It even provides a lot of valuable information about the host.
nmap -A <Domain_Name/DNS/Host_IP>

Here is the final output for. If you have any queries or questions, ask me in the comment.
Also Read : Using Python Steal Browser Data Of Anybody
Conclusion :
N-map is clearly a major part of the “Swiss Army Knife” of networking, thanks to its inventory of versatile commands. It lets you quickly scan and discover essential information about your network, hosts, ports, firewalls, and operating systems. N-map has numerous settings, flags, and preferences that help system administrators analyze a network in detail.
If you want to learn more about n-map and how it works and it;s various uses with scripts, check out their official website “N-map: the Network Mapper — Free Security Scanner”.
With this article, we have finished our “Network and port scanner” section of our Information gathering section.




