Introduction To Reverse Engineering android Apps

Reverse engineering, also known as reverse coding or back engineering, is the process of examining a software program or device to understand how it works and to make modifications to it.
In the case of Android apps, reverse engineering involves analyzing the source code of an app to understand its internal workings.
In this article, we will take a step-by-step approach to reverse engineering an Android app and provide you with the tools and techniques required to get started.
Understanding the Android App Ecosystem
Before diving into reverse engineering, it’s important to understand the Android app ecosystem and the structure of an Android app.
An Android app (.apk) is a package of files that are written in Java and organised into a specific structure. The structure of an Android app includes the following components:
- AndroidManifest.xml: This file contains information about the app, such as its name, version, and permissions.
- res/: This directory contains resources for the app, such as images, layouts, and strings.
- src/: This directory contains the Java source code for the app.
- libs/: This directory contains any libraries required by the app.
Also Read, How to Make Ransomware with Python in just 5 steps
Decompiling the APK File
The first step in reverse engineering an Android app is to decompile the APK file. An APK file is the package file format used by the Android operating system for the distribution and installation of Android apps.
To decompile the APK file, you can use a tool called apktool. Apktool is a tool for reverse engineering Android apk files. It can decode the resources to nearly original form and rebuild them after making some modifications.
To decompile an APK file using apktool, follow these steps:
- Download apktool from https://ibotpeaches.github.io/Apktool/.
- Open a terminal or command prompt and navigate to the directory where the APK file is stored.
- Run the following command: apktool d –no-src <apk name>
- Running the following command decompiles the resources and the XML files of the APK to human-readable form and the Java, Kotlin code to smali files.
- The binary resources and the XML files have been converted to their original form.

You can see the AndroidManifest.xml file now.

Also Read, How to Use : Nmap for ports and Network scanning?
Extracting the Code
The code is packed into .dex files. Dex stands for Dalvik Executable. A Dex file contains code that is ultimately executed by the Android Runtime.
In an Application, Dex files are generated based on the number of methods it has. The Dalvik Executable specification limits the total number of methods that can be referenced within a single DEX file to 65,536 — including Android framework methods, library methods, and methods in your code.
When the number of methods exceeds the limit, classes2.dex, classes3.dex files are generated.
We can convert dex files to jar files using the dex2jar tool. Download the dex2jar tool using the above link in the directory where apk was decompiled.
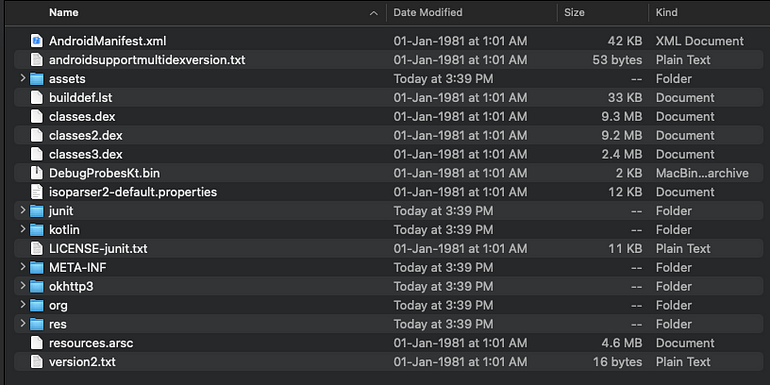
My folder structure looks like this, where the slide folder and dex2jar-2.0 folder are on the same directory.
*I renamed the apk to slide.apk for my convenience
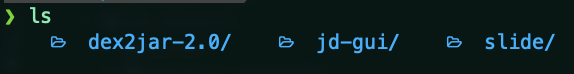
- In the terminal, move to the dex2jar folder and run these 2 scripts —
chmod u+x d2j_invoke.shandchmod u+x d2j-dex2jar.sh
This will enable you to run the dex2jar command and convert dex files to Java files. - Remember to rename your classes.dex file to app-name_classes.dex, because
classes-dex2jar.jaris used as a common name and will be overridden on the next dex2jar conversion. - Now run
./d2j-dex2jar.sh ../slide/slide_classes.dexinside dex2jar-2.0 folder. - This will create
slide_classes-dex2jar.jarfile inside your dex2jar-2.0 folder.
Congratulations, You have decompiled the apk, and now you can see the source code
Now you can use the JD-GUI tool to see the Java/Kotlin files inside the application.
- Open JD-GUI tool following the instructions written in this link.
- Using JD-GUI, open the slide_classes-dex2jar.jar file present inside the
dex2jar-2.0 folder.
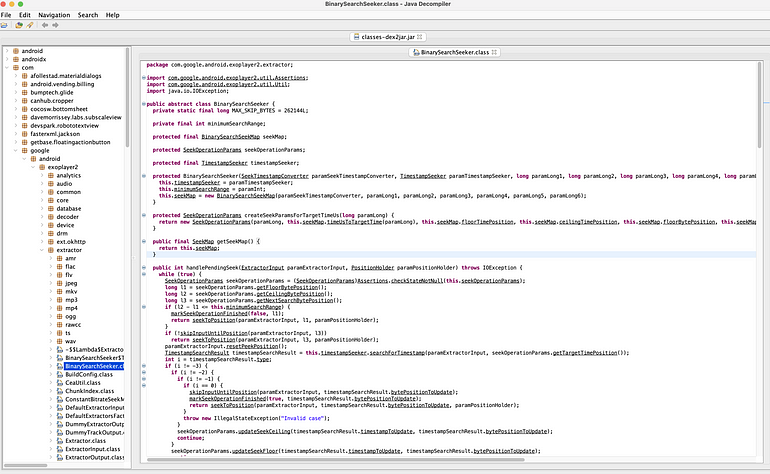
This is a really useful tool to explore your favourite android apps and to check how they have implemented the complex features.
Also Read : The Ultimate FREE Hack Pack : Over 100+ Hacking Tools for 2023
Conclusion
Reverse engineering an Android app can be a challenging but rewarding experience. By understanding the structure of an Android app, decompiling the APK file, and analyzing the code, you can gain a deeper understanding of how your favorite apps work and even make modifications to improve them.
We hope this article has provided you with the knowledge and tools you need to get started with reverse engineering Android apps. If you have any questions or comments, please leave them in the comments section below.




